ISO 27002, Cobit 4, SWIFT, NIST SP 800-53
What's RBox?
Modular software solution for Security Management. It allows information security to be aligned with business through risk assessment and management, regulatory compliance and business continuity, among others.
Software features
Ready-to-use standards
R-BOX has the unique feature of having ready to be added, the most of the security IT standards (ISO, NIST, COBIT, BCRA, SWIFT, etc). Our Standard Plug & Play system, allows that with minor configurations any well-known IT security standard are ready to be used by our customers.
Knowledge base
Based entirely on MAGERIT methodology, its robust entity model enables the fast definition of standards, controls, verifications and recommendations for the most important IT security and compliance standards.
Organization modeling
It allows the definition of the organizational model through its information flow; defining its assets, responsible people, maturity management and other attributes for a correct diagnosis of the IT risk situation.
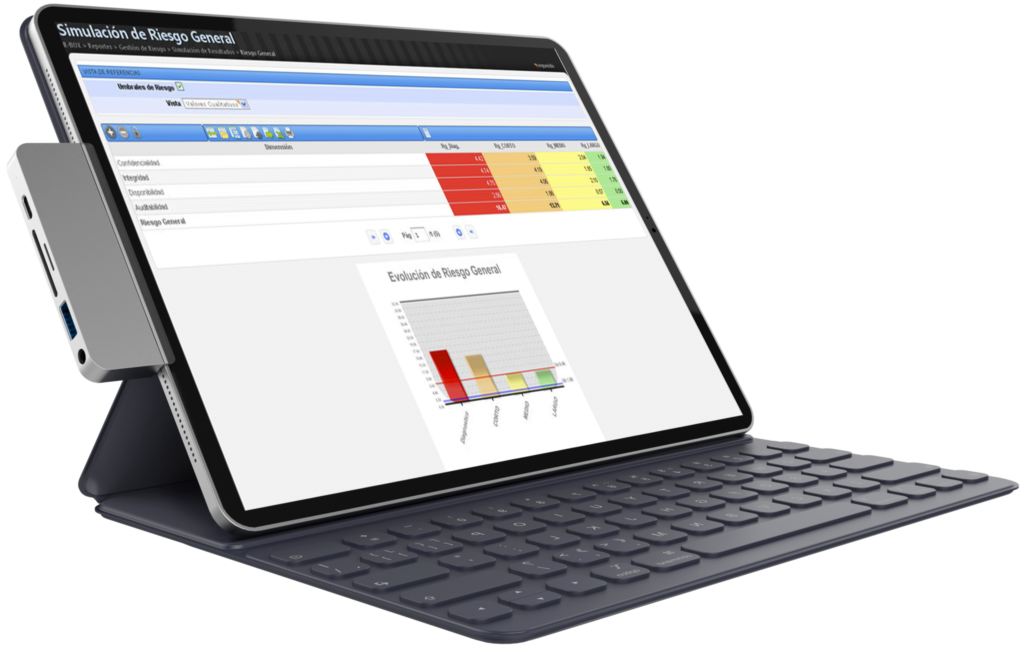
Solid math
R-Box includes a complex and elaborated calculation algorithm that differentiates it and stands out from its competitors. This information is well documented and available and for our clients.
WIde integration
RBOX can be integrated with other systems inside organization infrastructure, for example: Active Directory, incident management systems, operational risk systems, etc.
Want to know more?
Functionality
The functionality of RBOX is built from a series of modules that provides different services according to the needs of each organization.
Customers
© 2014 - 2022 Platinum Ciber-seguridad | All rights reserved











